Personal Access Tokens (PATs) are a secure way to authenticate into Azure DevOps when using tools like Git, REST APIs, or third-party integrations. This guide will walk you through the process of creating one. Once you have one, try using it in C# with our example How to connect to Azure DevOps with a personal access token in C#.
Scopes
When you create a Personal Access Token, you need to specify a scope. This specifies with operations can be performed with the token, e.g., which data it can read and write. You should use the minimum scope necessary for the application using the token.
For example, if you are only tracking work items, don’t give the PAT access to anything else. And if you are only reading work items, don’t give the PAT write permission. As a best practice you should grant the absolute minimum permissions possible.
- Code (Read, Write, Manage)
Access Git repositories for cloning, pushing, and managing branches and commits. - Work Items (Read, Write, Manage)
View, edit, and administer work items such as tasks, bugs, and user stories. - Build (Read, Execute, Manage)
Trigger builds, view build results, and manage build definitions and agents. - Release (Read, Execute, Manage)
Access and control release pipelines, deployments, and release environments. - Packaging (Read, Write, Manage)
Interact with Azure Artifacts feeds, including publishing and consuming packages. - Service Connections (Read, Manage)
View and configure service connections used in pipelines and integrations. - Project and Team (Read)
View project structure, team settings, and membership details. - Graph (Read)
Access organizational directory data such as users and groups. - Identity (Read)
Retrieve identity information like user profiles and authentication metadata. - Security (Manage)
Administer security roles, permissions, and access control settings. - Variable Groups (Read, Manage)
View and manage shared variable groups used in pipelines. - Tokens Administration (Manage)
Create, revoke, and manage other PATs (admin-only functionality). - Audit Log (Read)
View audit events for tracking changes and access history. - Agent Pools (Read, Manage)
Access and configure agent pools for build and release pipelines. - Extension Management (Read, Write)
Install, update, and manage Azure DevOps Marketplace extensions. - Member Entitlement Management (Read, Write)
View and modify user entitlements and license assignments. - Policy (Read, Write)
Access and configure branch policies and repository settings. - Process (Read, Write)
View and manage work item process templates and customization. - Profile (Read, Write)
Access and update user profile information. - Project Analysis (Read)
View analytics and reporting data for projects. - Release Management (Read, Write)
Manage release definitions and deployment settings. - Service Endpoint (Read, Write)
Configure service endpoints for external integrations. - Source Providers (Read)
Access source control provider configurations. - Task Groups (Read, Write)
Manage reusable task groups in build and release pipelines. - Test Management (Read, Write)
Access and manage test plans, test cases, and results. - Wiki (Read, Write)
View and edit project wikis and documentation. - YAML Pipelines (Read, Write)
Access and manage YAML-based pipeline definitions.
Good practices
A Personal Access Token is safer than a username and password because you can limit its scope and you can revoke the token at any time. However, you must still treat the token as highly sensitive and never store in directly in source code or a repository. Treat a PAT just as you would any other security credential.
Prerequisites
- You must have an Azure DevOps account.
- You must be signed into Azure DevOps.
Instructions
- Sign into your Azure DevOps organization
- Click the user settings icon next to your profile picture in the upper-right.

- Click Personal access tokens
- Click New Token
- Enter a name for the personal access token
Do not include personal information in the token name. Do not rename the token to include any part of the token value.
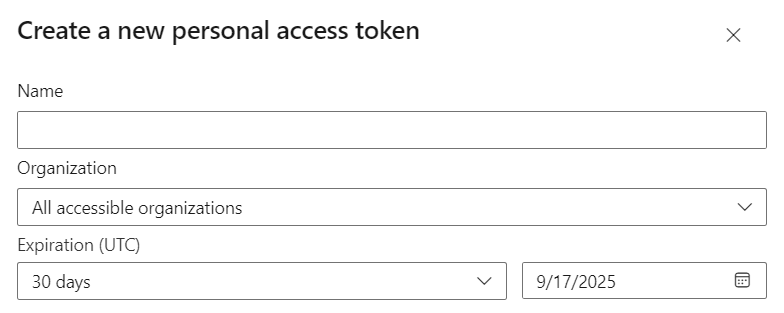
- Select your organization where you want to use the token
- Select an expiration length of the token
Keep your PAT lifetime short. Microsoft recommends a week or less.
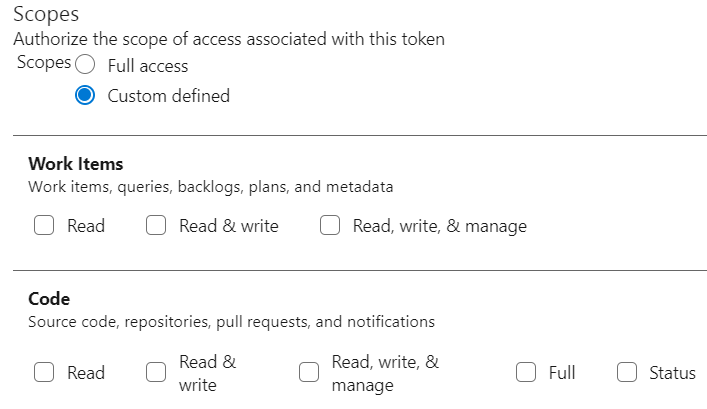
- Set the scope of the token
Scopes define what resources and operations your Personal Access Token (PAT) can access. You should grant the minimum access necessary for your use case. Avoid granting full access.
- Click Save
- Sign in with the token within 90 days or it may become inactive
Reference
- Azure DevOps PAT Documentation – Microsoft Learn – Official documentation for creating and using PATs. Includes scope descriptions, security recommendations and alternatives such as Microsoft Entra tokens.
Leave a Reply