One you have established an Azure Key Vault to store your secrets (such as a shared password or API key), you need to grant access to the vault so the users can fetch the secret as needed. Under the Azure RBAC model (role-based access control), you assign a role to a person who needs access. The role defines the permissions granted to the person.
Prerequisites
These instructions assume you have already created a key vault and now you need to grant someone access to the vault. If you still need to create the vault, see How to create an Azure Key Vault.
Instructions
- Go to your key vault on Azure
From the top search bar, you can search for your vault by name, or search for “key vaults” and navigate to your vault.
- Click Access Control (IAM) on the left menu
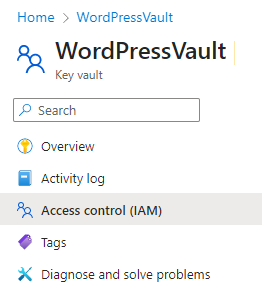
- Click +Add and then Add Role Assignment from the menu
- Click role you want to assign to the user (typically Key Vault Secrets User)
To view secrets (read-only), click Key Vault Secrets User. To create secrets, you need Key Vault Secrets Officer.
On a typical team, give the lead the Key Vaults Secrets Officer role. Give the team members Key Vaults Secrets User. This means the lead person can create the secrets, and the rest of the team has read-only access to read them. - Click Next
- Click + Select members
A popup window will appear for you to select one or more people to receive the role.
- In the popup, select a person and click Select
- Optionally write a description
A description of why you are assigning this role can be helpful for auditing purposes.
- Click Review + assign
- Review and click Review + assign again
Reference
- Azure Key Vault documentation | Microsoft Learn – top-level page of the Microsoft Azure Key Vault documentation.
- Grant permission to applications to access an Azure key vault using Azure RBAC | Microsoft Learn – Documentation on using the RBAC model (role-based access control) to manage permissions to a key vault. Includes a description of the built-in roles.
Leave a Reply