Once you’ve created an Azure Key Vault, you need to store a secret in it (such as a shared password or API key). If you haven’t created the vault yet, see How to create an Azure Key Vault. If you’ve already stored the secret and need to grant access, see How to grant access to secrets in an Azure Key Vault.
Definitions
An Azure Key Vault is a cloud service that securely stores sensitive information like secrets, encryption keys, and certificates. It helps safeguard access to these resources using fine-grained permissions.
A secret is a piece of data such as a password, connection string, API key, or any other sensitive information. Azure Key Vault can securely store these secrets for your later retrieval.
Instructions
- Go to your key vault on Azure
From the top search bar, you can search for your vault by name, or search for “key vaults” and navigate to your vault. If you need to create a key vault, see How to create an Azure Key Vault.
- In the left menu, expand Objects and select Secrets
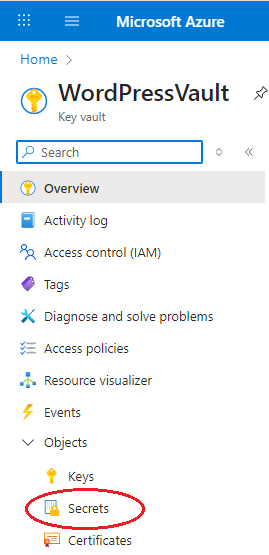
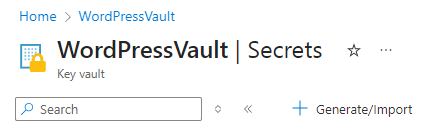
- Click +Generate/Import
- Specify the name of your secret
The name must consist of letters, numbers and dashes (no spaces), and cannot begin with a number.
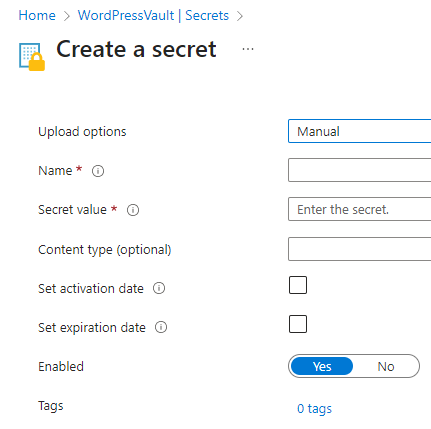
- Specify the secret value
- Optionally set a Content Type (typically blank)
The content type is an optional metadata field that describes the format or purpose of the secret’s value, e.g.,
"application/json"or"text/plain". You probably don’t need this unless you are a developer. It doesn’t affect how the secret is stored or accessed, but it can help applications interpret the data correctly. - Optionally set an activation date and/or expiration date (typically unset)
You can optionally set a date when the secret becomes active, and/or set a date when the secret is expired. These dates impact developers who are accessing the secret through API calls. Even if the secret is pre-activation or post-expiration, you can still view its value on the Azure portal.
- Optionally disable the secret (typically enabled)
You can also disable the secret right away. This impacts developers who are accessing the secret through API calls. If the secret is disabled, the API call will not retrieve the value. But even if the secret is disabled, it can still be viewed on the Azure portal.
- Click Create
Reference
- Azure Key Vault documentation | Microsoft Learn – Links to Azure Key Vault documentation.
- What is Azure Key Vault? | Microsoft Learn – basic concepts
Leave a Reply